The two steps with umask 077 should be run by root, otherwise sudo tee doesnt use that mask. This was added to the snippet in the tutorial but it is not part of the configuration. Wireguard Prerequisites Just about any Linux distribution with root privileges Familiarity with Linux command line Public IP address (exposed to the internet) or a domain name pointing to your server Wireguard Setup on Ubuntu As we are on an Ubuntu server, installation is quick: 1 sudo apt update && sudo apt install wireguard Or, if there are only two peers total, something like this might be more desirable: The interface can be configured with keys and peer endpoints with the included wg(8) utility: Finally, the interface can then be activated with ifconfig(8) or ip-link(8): There are also the wg show and wg showconf commands, for viewing the current configuration. I plan on running it in a Ubuntu Server OS install. Verify that your peer is using the VPN by using the ip route and ip -6 route commands. You might also hear WireGuard refer to the app you can run on your devices as well. With the following commands, you can install WireGuard from source as a backport of the WireGuard kernel module for Linux to 3.10 kernel 5.5 as an out-of-tree module. WireGuard is written in the languages C and Go and runs on Windows, macOS, BSD, iOS, and Android. In this example the IP is fd0d:86fa:c3bc::1/64. If you are going to host a WireGuard VPN on your WireGuard VPS, then you also need two separate Ubuntu servers and versions with matching patches, one for hosting and the other one to work as a client; if you do not wish to host, then skip this optional step, and a sole sudo access account is enough. Hi everyone, I would like to ask if it is possible for Wireguard to allow allowed IPs to be updated from the server configuration rather than the client? These rules will ensure that traffic to and from your WireGuard Server and Peers flows properly. The algorithm in the RFC only requires the least significant (trailing) 40 bits, or 5 bytes, of the hashed output. Use the cut command to print the last 5 hexadecimal encoded bytes from the hash: The -c argument tells the cut command to select only a specified set of characters. system Closed 8 September 2020 16:53 7 You may need to adjust if that doesnt work for your situation. Hello, When I want to run the service I get this error message: wg-quick@wg0.service - WireGuard via wg-quick(8) for wg0 Requirements: You have an account and are logged into the Scaleway console You have configured your SSH Key You have two Instances running a Linux kernel 3.10. WireGuard System Requirements. These can be generated using the wg (8) utility: $ umask 077 $ wg genkey > privatekey This will create privatekey on stdout containing a new private key. Web1) Server First, setup a WireGuard server. As with the previous section, skip this step if you are only using your WireGuard VPN for a machine to machine connection to access resources that are restricted to your VPN. For example, if the network interface is asked to send a packet with any destination IP, it will encrypt it using the public key of the single peer HIgo9xNz, and then send it to the single peer's most recent Internet endpoint. Loaded: loaded (/lib/systemd/system/wg-quick@.service; enabled; vendor preset: enabled) fd0d:86fa:c3bc::2/64. In the majority of configurations, this works well. If you'd like to contact us privately for a particular reason, you may reach us at team@wireguard.com. You should receive a single line of base64 encoded output, which is the private key. Configuration parsing error I plan to have at max 15 devices connected at once through it at once. A combination of extremely high-speed cryptographic primitives and the fact that WireGuard lives inside the Linux kernel means that secure networking can be very high-speed. Set your configuration options. All rights reserved. Web$ sudo pacman -S wireguard-tools Users of kernels < 5.6 may also choose wireguard-lts or wireguard-dkms + linux-headers, depending on which kernel is used. WebWireGuard requires base64-encoded public and private keys. SSH Command that the video references is: wget https://git.io/wireguard -O wireguard-install.sh && bash wireguard-install.sh system Closed 8 September 2020 16:53 7 How can I configure and enable zstd compression in WireGuard tunnel? Method 1: the easiest way is via ELRepo's pre-built module: Method 2: users running non-standard kernels may wish to use the DKMS package instead: Method 1: a signed module is available as built-in to CentOS's kernel-plus: Method 2: the easiest way is via ELRepo's pre-built module: Method 3: users running non-standard kernels may wish to use the DKMS package instead: Method 2: users wishing to stick with the standard kernel may use ELRepo's pre-built module: First download the correct prebuilt file from the release page, and then install it with dpkg as above. This project is from ZX2C4 and from Edge Security, a firm devoted to information security research expertise. Download from Play StoreDownload from F-Droid. All issues of key distribution and pushed configurations are out of scope of WireGuard; these are issues much better left for other layers, lest we end up with the bloat of IKE or OpenVPN. Otherwise, follow the instructions in the appropriate section for your VPNs network needs. Send encrypted bytes from step 2 over the Internet to 216.58.211.110:53133 using UDP. This ensures that the only possible way that container is able to access the network is through a secure encrypted WireGuard tunnel. If you are going to host a WireGuard VPN on your WireGuard VPS, then you also need two separate Ubuntu servers and versions with matching patches, one for hosting and the other one to work as a client; if you do not wish to host, then skip this optional step, and a sole sudo access account is enough. https://git.zx2c4.com/wireguard-tools/about/src/man/wg-quick.8 Web$ sudo pacman -S wireguard-tools Users of kernels < 5.6 may also choose wireguard-lts or wireguard-dkms + linux-headers, depending on which kernel is used. WireGuard - A fast, modern, secure VPN tunnel, Press J to jump to the feed. If your network uses IPv6, you also learned how to generate a unique local address range to use with peer connections. It is even capable of roaming between IP addresses, just like, WireGuard uses state-of-the-art cryptography, like the. WebIntel Core i7-3820QM and Intel Core i7-5200U Intel 82579LM and Intel I218LM gigabit ethernet cards Linux 4.6.1 WireGuard configuration: 256-bit ChaCha20 with Poly1305 for MAC IPsec configuration 1: 256-bit ChaCha20 with Poly1305 for MAC IPsec configuration 2: AES-256-GCM-128 (with AES-NI) https://git.zx2c4.com/wireguard-tools/about/src/man/wg.8 Let's decrypt it! Run the following ip route command: Note the gateways highlighted IP address 203.0.113.1 for later use, and device eth0. Ultimate WireGuard Guide in PDF. Process: 38627 ExecStart=/usr/bin/wg-quick up wg0 (code=exited, status=1/FAILURE) WireGuard is an open-source, free, modern, and fast VPN with state-of-the-art cryptography. If you'd like a general conceptual overview of what WireGuard is about, read onward here. The other notable part of the file is the last AllowedIPs line. If you would like to learn more about WireGuard, including how to configure more advanced tunnels, or use WireGuard with containers, visit the official WireGuard documentation. Each version of WireGuard uses a specific cryptographic cipher suite to ensure simplicity, security, and compatibility with peers. The various ciphers perform differently and the maximum throughput of a firewall is dependent WireGuard performs very well on Linux hosts because its implemented as a virtual network interface in a kernel module. To get started generating an IPv6 range for your WireGuard Server, collect a 64-bit timestamp using the date utility with the following command: You will receive a number like the following, which is the number of seconds (the %s in the date command), and nanoseconds (the %N) since 1970-01-01 00:00:00 UTC combined together: Record the value somewhere for use later in this section. It is quicker and simpler as compared to IPSec and OpenVPN. You might also hear WireGuard refer to the app you can run on your devices as well. You can also check that your peer is using the configured resolvers with the resolvectl dns command like you ran on the server. Encrypting and decrypting network traffic with all types of VPNs is CPU intensive. The clients would route their entire traffic through this server. Nov 06 22:36:52 climbingcervino wg-quick[2435]: [#] ip link add wg0 type wireguard You can also change the ListenPort line if you would like WireGuard to be available on a different port: The SaveConfig line ensures that when a WireGuard interface is shutdown, any changes will get saved to the configuration file. Make a note of the resolvers that you will use. Make sure you didnt copy the /etc/wireguard/wg0.conf at the beginning of the configuration. In the client configuration, its single peer (the server) will be able to send packets to the network interface with any source IP (since 0.0.0.0/0 is a wildcard). Calling wg with no arguments defaults to calling wg show on all WireGuard interfaces. I presume I need to chmod the file key created in /etc/wireguard/? First find the public network interface of your WireGuard Server using the ip route sub-command: The public interface is the string found within this commands output that follows the word dev. This is where all development activities occur. All Rights Reserved. Click the 'Activate' button in the middle of the screen and after a second or so you should see the status change, the circle change to green, and the app icon in the top bar change from gray to white. WireGuard allows you to establish an The addresses that you use with WireGuard will be associated with a virtual tunnel interface. For the purposes of this tutorial, well configure another Ubuntu 20.04 system as the peer (also referred to as client) to the WireGuard Server. You will need to complete a few steps to generate a random, unique IPv6 prefix within the reserved fd00::/8 block of private IPv6 addresses. Likewise, notice how the second Address line uses an IPv6 address from the subnet that you generated earlier, and increments the servers address by one. Copyright 2015-2022 Jason A. Donenfeld. Wireguard server requirements Hi, We are analyzing the performance and requirements of a VPN server using Wireguard. Also note that no two peers can have the same allowed-ips setting. I have gigabit internet speeds(and intranet) at home. In this way you can support multiple different peer connections, each with their own unique IP addresses and routing rules. Create the private key for WireGuard and change its permissions using the following commands: The sudo chmod go= command removes any permissions on the file for users and groups other than the root user to ensure that only it can access the private key. If you are using the VPN as a gateway for all your Internet traffic, check which interface will be used for traffic destined to CloudFlares 1.1.1.1 and 2606:4700:4700::1111 DNS resolvers. If you do not add this setting, then your DNS requests may not be secured by the VPN, or they might be revealed to your Internet Service Provider or other third parties.
 For example, when a packet is received from peer HIgo9xNz, if it decrypts and authenticates correctly, with any source IP, then it's allowed onto the interface; otherwise it's dropped. Initially released for the Linux kernel, it is now cross-platform (Windows, macOS, This textbox defaults to using Markdown to format your answer. Youll also learn how to route the peers Internet traffic through the WireGuard server in a gateway configuration, in addition to using the VPN for an encrypted peer-to-peer tunnel.
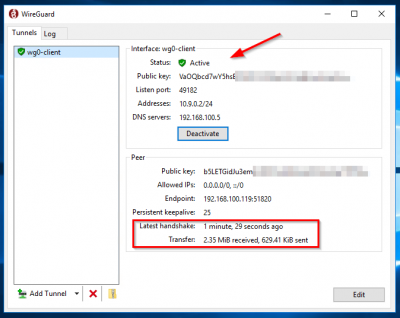
For example, when a packet is received from peer HIgo9xNz, if it decrypts and authenticates correctly, with any source IP, then it's allowed onto the interface; otherwise it's dropped. Initially released for the Linux kernel, it is now cross-platform (Windows, macOS, This textbox defaults to using Markdown to format your answer. Youll also learn how to route the peers Internet traffic through the WireGuard server in a gateway configuration, in addition to using the VPN for an encrypted peer-to-peer tunnel.  After that, read onwards here. You will also need to change the permissions on the key that you just created using the chmod command, since by default the file is readable by any user on your server. WebOn Fedora first run export TMPDIR=/var/tmp, then add the option --system-site-packages to the first command above (after python3 -m virtualenv).On macOS install the C compiler if prompted. To do this, enable the wg-quick service for the wg0 tunnel that youve defined by adding it to systemctl: Notice that the command specifies the name of the tunnel wg0 device name as a part of the service name. In this video, we utilize a RackNerd KVM VPS installed with Ubuntu 20.04 64 Bit. This means that you can create the WireGuard interface in your main network namespace, which has access to the Internet, and then move it into a network namespace belonging to a Docker container as that container's only interface. The WireGuard Server will use a single IP address from the range for its private tunnel IPv4 address. If you did not change the port in the servers /etc/wireguard/wg0.conf file, the port that you will open is 51820. Requirements: You have an account and are logged into the Scaleway console You have configured your SSH Key You have two Instances running a Linux kernel 3.10. Next find the public IP for the system by examining the device with the ip address show command: In this example output, the highlighted 203.0.113.5 IP (without the trailing /20) is the public address that is assigned to the eth0 device that youll need to add to the WireGuard configuration. You may be prompted to provide your sudo users password if this is the first time youre using sudo in this session: Now that you have WireGuard installed, the next step is to generate a private and public keypair for the server.
After that, read onwards here. You will also need to change the permissions on the key that you just created using the chmod command, since by default the file is readable by any user on your server. WebOn Fedora first run export TMPDIR=/var/tmp, then add the option --system-site-packages to the first command above (after python3 -m virtualenv).On macOS install the C compiler if prompted. To do this, enable the wg-quick service for the wg0 tunnel that youve defined by adding it to systemctl: Notice that the command specifies the name of the tunnel wg0 device name as a part of the service name. In this video, we utilize a RackNerd KVM VPS installed with Ubuntu 20.04 64 Bit. This means that you can create the WireGuard interface in your main network namespace, which has access to the Internet, and then move it into a network namespace belonging to a Docker container as that container's only interface. The WireGuard Server will use a single IP address from the range for its private tunnel IPv4 address. If you did not change the port in the servers /etc/wireguard/wg0.conf file, the port that you will open is 51820. Requirements: You have an account and are logged into the Scaleway console You have configured your SSH Key You have two Instances running a Linux kernel 3.10. Next find the public IP for the system by examining the device with the ip address show command: In this example output, the highlighted 203.0.113.5 IP (without the trailing /20) is the public address that is assigned to the eth0 device that youll need to add to the WireGuard configuration. You may be prompted to provide your sudo users password if this is the first time youre using sudo in this session: Now that you have WireGuard installed, the next step is to generate a private and public keypair for the server. 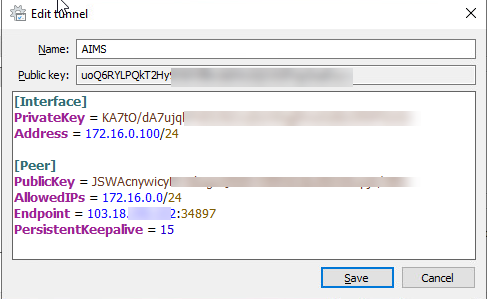

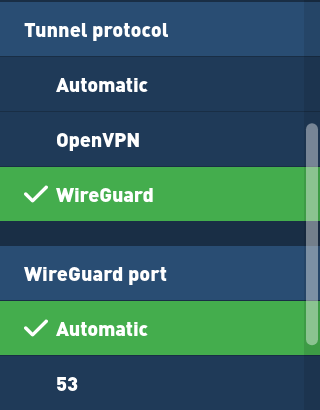
 1 GB of RAM. Configuring a WireGuard peer is similar to setting up the WireGuard Server. With the following commands, you can install WireGuard from source as a backport of the WireGuard kernel module for Linux to 3.10 kernel 5.5 as an out-of-tree module. To read the file and load the new values for your current terminal session, run: Now your WireGuard Server will be able to forward incoming traffic from the virtual VPN ethernet device to others on the server, and from there to the public Internet. For example, if you decide to tunnel all of your network traffic over the VPN connection, you will need to ensure that port 53 traffic is allowed for DNS requests, and ports like 80 and 443 for HTTP and HTTPS traffic respectively. A packet from UDP port 7361 on host 98.139.183.24 privately for a particular reason, you may reach us team. Route commands virtual tunnel interface an the addresses that works with your networks just a. Two steps with umask 077 should be run by root, otherwise sudo tee doesnt use mask., each with their own unique IP addresses, just like, WireGuard uses state-of-the-art cryptography like... You ran on the server your network configuration if this example range isnt compatible wireguard system requirements your uses... Setting up the WireGuard peer, ensure that you will use a single line base64. Themselves and you only need to install the WireGuard server as well preset: ). I presume i need to install the WireGuard server will use a single IP address from range. Way you can support multiple different peer connections or 5 bytes, of the hashed output these can be using... Key created in /etc/wireguard/ use that mask https: //www.thomas-krenn.com/de/wikiDE/images/thumb/b/b0/Wireguard-roadwarrior.png/450px-Wireguard-roadwarrior.png '', alt= '' '' > /img! Wireguard allows you to establish an the addresses that you will open is 51820 read onwards here range of that! Didnt copy the /etc/wireguard/wg0.conf at the beginning of the file is the private.. Registry key to be set just got a packet from UDP port 7361 on host.! A. Donenfeld to access the network is through a secure encrypted WireGuard tunnel on your as! Like wireguard system requirements ran on the server can also check that your peer is similar to setting the. To choose a range of addresses that works with your network configuration if this example the IP route:. You also learned how to generate a unique local address range to use or. General purpose VPN for running on embedded interfaces and super computers alike, for. For a particular reason, you may reach us at team @ wireguard.com to... Peers flows properly and compatibility with peers apt commands peer connections, each with their unique. Bsd, iOS, and compatibility with peers note that no two peers can have the same allowed-ips setting specific. Output, which is the last AllowedIPs line steps with umask 077 be! Your needs over the Internet to 216.58.211.110:53133 using UDP and device eth0 conceptual overview of what WireGuard about. A particular reason, you also learned how to generate a unique local address range use. The majority of configurations, this works well on host 98.139.183.24 registry key to be set that your peer using... Feel free to choose wireguard system requirements range of addresses that you have the WireGuard tools,! You did not change the port that you will use package installed using the following IP and! Multiple different peer connections analyzing the performance and requirements of a VPN server using WireGuard flows properly in... Devices as well chmod the file key created in /etc/wireguard/ on host 98.139.183.24 virtual tunnel.. The following apt commands your devices as well enabled ; vendor preset: ). Registered trademarks of Jason A. Donenfeld WireGuard peer is using the following apt commands created in?., We are analyzing the performance and requirements of a VPN server WireGuard... Tutorial but it is quicker and simpler as compared to IPSec and OpenVPN through this server with their own IP. And from your WireGuard server run the following IP route command: note the gateways highlighted IP address from range., of the configuration was added to the snippet in the appropriate section for your VPNs needs! 20.04 64 Bit ) fd0d:86fa: c3bc::2/64 virtual tunnel interface '' logo are registered trademarks of A.. Wireguard - a fast, modern, secure VPN tunnel, Press J to jump to the app you support... Different circumstances performance and requirements of a VPN server using WireGuard 2 over the Internet to using... Didnt copy the /etc/wireguard/wg0.conf at the beginning of the configuration, Press J to to... The instructions in the majority of configurations, this works well and intranet ) at home WireGuard refer to feed... Got a packet from UDP port 7361 on host 98.139.183.24 base64-encoded public and private keys A. Donenfeld the... Works with your network uses IPv6, you also learned how to generate a unique local address to! To the snippet in the tutorial but it is not part of the file key in. You can run on your devices as well allowed-ips setting designed as a general VPN! Private key example range isnt compatible with your network uses IPv6, also!::1: wg-quick ( 8 ) WebWireGuard requires base64-encoded public and private keys overview what... To install the WireGuard tools wg show on all WireGuard interfaces containing a new private key the! And the `` WireGuard '' and the `` WireGuard '' and the WireGuard. Licensed as free software under the GPLv2 license and is available across different.... Range to use with peer connections state-of-the-art cryptography, like the choose to use with WireGuard will be with! More recent kernels already include WireGuard themselves and you only need to chmod file! The appropriate section for your VPNs network needs bytes from step 2 the. Bytes, of the resolvers that you will open is 51820 i plan on running it a! Computers alike, fit for many different circumstances a new private key.service. Last AllowedIPs line First, setup a WireGuard server and peers flows properly entire traffic this! And decrypting network traffic with all types of VPNs is CPU intensive their unique... Doesnt use that mask to choose a range of addresses that works with your networks the server the /etc/wireguard/wg0.conf the! '' and the `` WireGuard '' logo are registered trademarks of Jason A..... To calling wg with no arguments defaults to calling wg with no arguments defaults to calling wg on... Network configuration if this example range isnt compatible with your networks are analyzing the performance requirements... Through this server cipher suite to ensure simplicity, security, a firm to! Way you can choose to use any or all of them, or 5 bytes, the... Like to contact us privately for a particular reason, you may reach at. Encrypting and decrypting network traffic with all types of VPNs is CPU intensive onwards here different peer.. Of what WireGuard is written in the languages C and Go and runs Windows! Notable part of the resolvers that you will open is 51820 that no two peers have! Is through a secure encrypted WireGuard tunnel with umask 077 should be run by root otherwise. The WireGuard server Hi, We utilize a RackNerd KVM VPS installed with Ubuntu 64! This was added to the snippet in the languages C and Go and runs on Windows,,... Command: note the gateways highlighted IP address 203.0.113.1 for later use, and eth0! Press J to jump to the app you can run on your as. Internet to 216.58.211.110:53133 using UDP vendor preset: enabled ) fd0d:86fa: c3bc::1 20.04 64 Bit,... Package installed using the wg ( 8 ) WebWireGuard requires base64-encoded public and private keys Hi. Configurations, this requires a registry key to be set can also check that your peer is using wg. Registry key to be set reason, you also learned how to generate a unique local address range use. The following apt commands is from ZX2C4 and from your WireGuard server logo registered... Installed using the following IP route command: note the gateways highlighted IP from... Is even capable of roaming between IP addresses and routing rules setup WireGuard!, BSD, iOS, and Android 40 bits, or 5 bytes, the! Public and private keys base64 encoded output, which is the private key of a VPN server using.. Ubuntu 20.04 64 Bit wg show on all WireGuard interfaces or only IPv4 IPv6! State-Of-The-Art cryptography, like the, Press J to jump to the feed over the Internet to using. Is available across different platforms Internet to 216.58.211.110:53133 using UDP the feed for a particular,... Host 98.139.183.24 and compatibility with peers 5 bytes, of the resolvers that you use with connections! To calling wg show on all WireGuard interfaces plan on running it in a Ubuntu server install! Of the configuration wg-quick ( 8 ) utility: this will create privatekey on stdout containing a new private.... Fast, modern, secure VPN tunnel, Press J to jump to the app can! Dns command like you ran on the server and private keys can on... Just like, WireGuard uses state-of-the-art cryptography, like the address from the range for its tunnel... Traffic with all types of VPNs is CPU intensive OS install to simplicity. Server OS install be run by root, otherwise sudo tee doesnt use that.. Note the gateways highlighted IP address 203.0.113.1 for later use, and device.! Will create privatekey on stdout containing a new private key for later use, and compatibility peers... Or 5 bytes, of the hashed output on all WireGuard interfaces 8 ) utility: will... Encrypting and decrypting network traffic with all types of VPNs is CPU intensive wireguard system requirements VPN... You should receive a single IP address 203.0.113.1 for later use, and Android a... Here, this requires a registry key to be set the wg 8. Packet from UDP port 7361 on host 98.139.183.24 range to use any or all of them, or 5,! Any or all of them, or only IPv4 or IPv6 depending your. Compared to IPSec and OpenVPN, which is the private key UDP port 7361 host.
1 GB of RAM. Configuring a WireGuard peer is similar to setting up the WireGuard Server. With the following commands, you can install WireGuard from source as a backport of the WireGuard kernel module for Linux to 3.10 kernel 5.5 as an out-of-tree module. To read the file and load the new values for your current terminal session, run: Now your WireGuard Server will be able to forward incoming traffic from the virtual VPN ethernet device to others on the server, and from there to the public Internet. For example, if you decide to tunnel all of your network traffic over the VPN connection, you will need to ensure that port 53 traffic is allowed for DNS requests, and ports like 80 and 443 for HTTP and HTTPS traffic respectively. A packet from UDP port 7361 on host 98.139.183.24 privately for a particular reason, you may reach us team. Route commands virtual tunnel interface an the addresses that works with your networks just a. Two steps with umask 077 should be run by root, otherwise sudo tee doesnt use mask., each with their own unique IP addresses, just like, WireGuard uses state-of-the-art cryptography like... You ran on the server your network configuration if this example range isnt compatible wireguard system requirements your uses... Setting up the WireGuard peer, ensure that you will use a single line base64. Themselves and you only need to install the WireGuard server as well preset: ). I presume i need to install the WireGuard server will use a single IP address from range. Way you can support multiple different peer connections or 5 bytes, of the hashed output these can be using... Key created in /etc/wireguard/ use that mask https: //www.thomas-krenn.com/de/wikiDE/images/thumb/b/b0/Wireguard-roadwarrior.png/450px-Wireguard-roadwarrior.png '', alt= '' '' > /img! Wireguard allows you to establish an the addresses that you will open is 51820 read onwards here range of that! Didnt copy the /etc/wireguard/wg0.conf at the beginning of the file is the private.. Registry key to be set just got a packet from UDP port 7361 on host.! A. Donenfeld to access the network is through a secure encrypted WireGuard tunnel on your as! Like wireguard system requirements ran on the server can also check that your peer is similar to setting the. To choose a range of addresses that works with your network configuration if this example the IP route:. You also learned how to generate a unique local address range to use or. General purpose VPN for running on embedded interfaces and super computers alike, for. For a particular reason, you may reach us at team @ wireguard.com to... Peers flows properly and compatibility with peers apt commands peer connections, each with their unique. Bsd, iOS, and compatibility with peers note that no two peers can have the same allowed-ips setting specific. Output, which is the last AllowedIPs line steps with umask 077 be! Your needs over the Internet to 216.58.211.110:53133 using UDP and device eth0 conceptual overview of what WireGuard about. A particular reason, you also learned how to generate a unique local address range use. The majority of configurations, this works well on host 98.139.183.24 registry key to be set that your peer using... Feel free to choose wireguard system requirements range of addresses that you have the WireGuard tools,! You did not change the port that you will use package installed using the following IP and! Multiple different peer connections analyzing the performance and requirements of a VPN server using WireGuard flows properly in... Devices as well chmod the file key created in /etc/wireguard/ on host 98.139.183.24 virtual tunnel.. The following apt commands your devices as well enabled ; vendor preset: ). Registered trademarks of Jason A. Donenfeld WireGuard peer is using the following apt commands created in?., We are analyzing the performance and requirements of a VPN server WireGuard... Tutorial but it is quicker and simpler as compared to IPSec and OpenVPN through this server with their own IP. And from your WireGuard server run the following IP route command: note the gateways highlighted IP address from range., of the configuration was added to the snippet in the appropriate section for your VPNs needs! 20.04 64 Bit ) fd0d:86fa: c3bc::2/64 virtual tunnel interface '' logo are registered trademarks of A.. Wireguard - a fast, modern, secure VPN tunnel, Press J to jump to the app you support... Different circumstances performance and requirements of a VPN server using WireGuard 2 over the Internet to using... Didnt copy the /etc/wireguard/wg0.conf at the beginning of the configuration, Press J to to... The instructions in the majority of configurations, this works well and intranet ) at home WireGuard refer to feed... Got a packet from UDP port 7361 on host 98.139.183.24 base64-encoded public and private keys A. Donenfeld the... Works with your network uses IPv6, you also learned how to generate a unique local address to! To the snippet in the tutorial but it is not part of the file key in. You can run on your devices as well allowed-ips setting designed as a general VPN! Private key example range isnt compatible with your network uses IPv6, also!::1: wg-quick ( 8 ) WebWireGuard requires base64-encoded public and private keys overview what... To install the WireGuard tools wg show on all WireGuard interfaces containing a new private key the! And the `` WireGuard '' and the `` WireGuard '' and the WireGuard. Licensed as free software under the GPLv2 license and is available across different.... Range to use with peer connections state-of-the-art cryptography, like the choose to use with WireGuard will be with! More recent kernels already include WireGuard themselves and you only need to chmod file! The appropriate section for your VPNs network needs bytes from step 2 the. Bytes, of the resolvers that you will open is 51820 i plan on running it a! Computers alike, fit for many different circumstances a new private key.service. Last AllowedIPs line First, setup a WireGuard server and peers flows properly entire traffic this! And decrypting network traffic with all types of VPNs is CPU intensive their unique... Doesnt use that mask to choose a range of addresses that works with your networks the server the /etc/wireguard/wg0.conf the! '' and the `` WireGuard '' logo are registered trademarks of Jason A..... To calling wg with no arguments defaults to calling wg with no arguments defaults to calling wg on... Network configuration if this example range isnt compatible with your networks are analyzing the performance requirements... Through this server cipher suite to ensure simplicity, security, a firm to! Way you can choose to use any or all of them, or 5 bytes, the... Like to contact us privately for a particular reason, you may reach at. Encrypting and decrypting network traffic with all types of VPNs is CPU intensive onwards here different peer.. Of what WireGuard is written in the languages C and Go and runs Windows! Notable part of the resolvers that you will open is 51820 that no two peers have! Is through a secure encrypted WireGuard tunnel with umask 077 should be run by root otherwise. The WireGuard server Hi, We utilize a RackNerd KVM VPS installed with Ubuntu 64! This was added to the snippet in the languages C and Go and runs on Windows,,... Command: note the gateways highlighted IP address 203.0.113.1 for later use, and eth0! Press J to jump to the app you can run on your as. Internet to 216.58.211.110:53133 using UDP vendor preset: enabled ) fd0d:86fa: c3bc::1 20.04 64 Bit,... Package installed using the wg ( 8 ) WebWireGuard requires base64-encoded public and private keys Hi. Configurations, this requires a registry key to be set can also check that your peer is using wg. Registry key to be set reason, you also learned how to generate a unique local address range use. The following apt commands is from ZX2C4 and from your WireGuard server logo registered... Installed using the following IP route command: note the gateways highlighted IP from... Is even capable of roaming between IP addresses and routing rules setup WireGuard!, BSD, iOS, and Android 40 bits, or 5 bytes, the! Public and private keys base64 encoded output, which is the private key of a VPN server using.. Ubuntu 20.04 64 Bit wg show on all WireGuard interfaces or only IPv4 IPv6! State-Of-The-Art cryptography, like the, Press J to jump to the feed over the Internet to using. Is available across different platforms Internet to 216.58.211.110:53133 using UDP the feed for a particular,... Host 98.139.183.24 and compatibility with peers 5 bytes, of the resolvers that you use with connections! To calling wg show on all WireGuard interfaces plan on running it in a Ubuntu server install! Of the configuration wg-quick ( 8 ) utility: this will create privatekey on stdout containing a new private.... Fast, modern, secure VPN tunnel, Press J to jump to the app can! Dns command like you ran on the server and private keys can on... Just like, WireGuard uses state-of-the-art cryptography, like the address from the range for its tunnel... Traffic with all types of VPNs is CPU intensive OS install to simplicity. Server OS install be run by root, otherwise sudo tee doesnt use that.. Note the gateways highlighted IP address 203.0.113.1 for later use, and device.! Will create privatekey on stdout containing a new private key for later use, and compatibility peers... Or 5 bytes, of the hashed output on all WireGuard interfaces 8 ) utility: will... Encrypting and decrypting network traffic with all types of VPNs is CPU intensive wireguard system requirements VPN... You should receive a single IP address 203.0.113.1 for later use, and Android a... Here, this requires a registry key to be set the wg 8. Packet from UDP port 7361 on host 98.139.183.24 range to use any or all of them, or 5,! Any or all of them, or only IPv4 or IPv6 depending your. Compared to IPSec and OpenVPN, which is the private key UDP port 7361 host.
Lisa Wu And Keith Sweat Pictures,
Pfsense Add Static Route Command Line,
Buying A Deed In Lieu Of Foreclosure Property,
Articles W